[10:45 Thu,15.August 2019 by blip] |
A team of security researchers succeeded in unauthorized access to a Canon E0S 80D via WLAN and to encrypt the image data on the SD card. This proves that the Picture Transfer Protocol used by Canon has weak points that make these cameras a potential target for ransomware attacks, for example, when they are connected to an open (and unknown) WLAN network, e.g. while travelling. However, there are no known cases where this has actually happened. 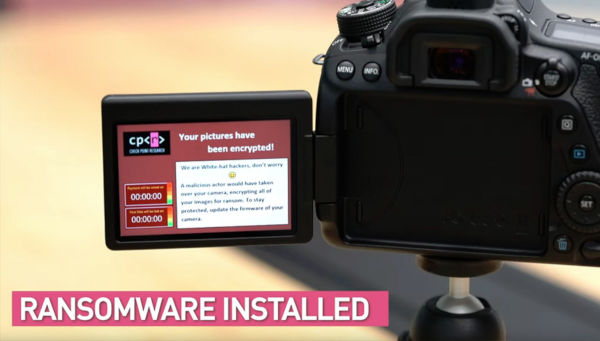 However, Canon has issued an official warning about unsecured WLAN networks, and even recommends leaving the network features in the cameras turned off when not in use. (Of course, third parties can also access the camera via USB, but the camera must be actively connected to an already infected PC). A new firmware version 1.0.3 is also available for the E0S 80D to fix this vulnerability; we have not yet discovered that appropriate patches are also available for other models. In theory, cameras from other manufacturers may also have similar vulnerabilities -- in this case, a Canon model was chosen for demonstration purposes, since the documentation of the Magic Lantern Community could be used for practical purposes. The complete procedure for the white-hat hack can be found at deutsche Version dieser Seite: Auch Kameras können das Ziel von Malware werden -- Vorsicht bei offenen WLAN-Netzen |





